Distributed API Security Framework
How It Works
PoC for a framework that provides real-time threat reporting and threat intelligence sharing across a distributed network of APIs using multiple protocols. Leverages RabbitMQ for messaging and uses a central hub for threat normalization. Anonymization soon.
Central Hub
The Central Hub acts as the core processor, receiving threat reports from multiple APIs and distributing the normalized data back to all participants. The hub is responsible for:
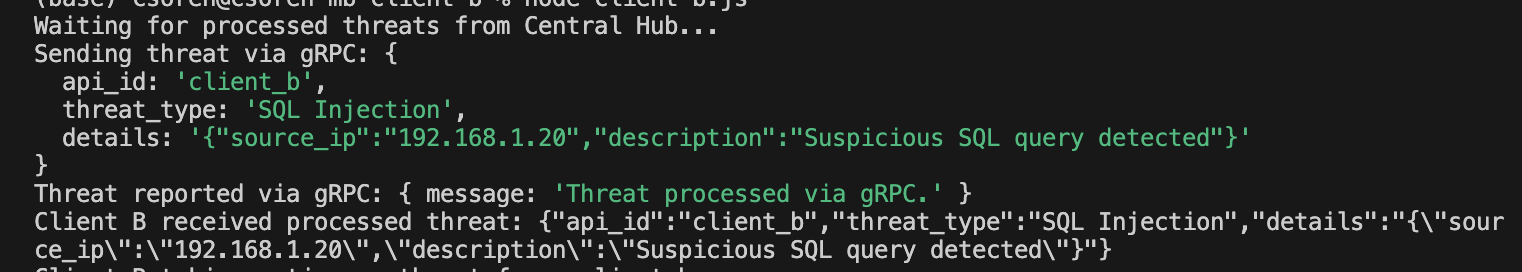
- Threat Processing: Incoming threat reports (from REST, gRPC, GraphQL) are converted into a standardized format (JSON) to ensure consistency.
- Threat Sharing: The processed reports are distributed to all other APIs in the network via RabbitMQ, enabling real-time collaboration.
RabbitMQ Message Broker
The RabbitMQ Message Broker handles real-time communication between APIs and the central hub. It facilitates the secure and efficient delivery of threat data by:
- Scalability: RabbitMQ can scale to handle a high volume of threat messages, ensuring that data is delivered without delay.
- Message Queueing: It queues messages from APIs and ensures that they are delivered to the central hub, even during high traffic.
Multi-Protocol Support
Emphasizing cross-collaboration from completely independent entities, the system supports multiple communication protocols, allowing APIs to report and receive threats using their preferred protocol:
- REST: Simple HTTP-based communication.
- gRPC: High-performance RPC framework, ideal for handling large volumes of data.
- GraphQL: A flexible query language for APIs, allowing fine-tuned requests.
Threat Normalization
Threat reports can be submitted in various formats based on the API protocol, but they are normalized into a standard JSON output by the central hub. This makes it easy for all participating APIs to interpret the data and respond appropriately, regardless of the original protocol used to submit the threat.
Anonymization
To maintain privacy while encouraging cross-organizational collaboration, each participating API is assigned an anonymized ID. This ensures that organizations can report and share threat intelligence without exposing sensitive information.
Network Effects
The network effects of this framework become increasingly powerful as more APIs join the system.
Next
Looking to the future, this framework could evolve into a decentralized model, incorporating trust ranking systems and integrating with blockchain.
